The CIA Triad Isn’t Dead—It’s Just Not Enough
Black Paper – 3C Layered Information Security Model
For decades we’ve treated “Confidentiality, Integrity, Availability” like gospel. It made sense when we lived inside tidy data centers with castle-and-moat networks. But that world’s gone. Today it’s cloud sprawl, third-party code stitched together with duct tape, AI everywhere, and attackers who treat your supply chain like an open bar.
I’m not anti-CIA. I’m anti-pretending it still covers the full blast radius. If your security story starts and ends with those three letters, you’re driving a 1980s map through a 2025 city.
Here’s how I think about it now.
The simple test: would CIA alone have saved you?
Ransomware is the easy example. “Availability” asks, is the system up? Cute. The real question is: can we survive the hit and get back online without paying? That’s resilience. If you don’t have immutable backups, an isolated recovery environment, and practiced muscle memory to restore fast, “availability” is a vanity metric.
Deepfakes are another. On paper, that audio file of your “CEO” authorizing a wire has perfect integrity. Checksums are happy. But it’s not authentic. CIA doesn’t have a field for “this is fake but technically unaltered.”
Identity, provenance, recovery—these aren’t side quests anymore. They’re the main story.
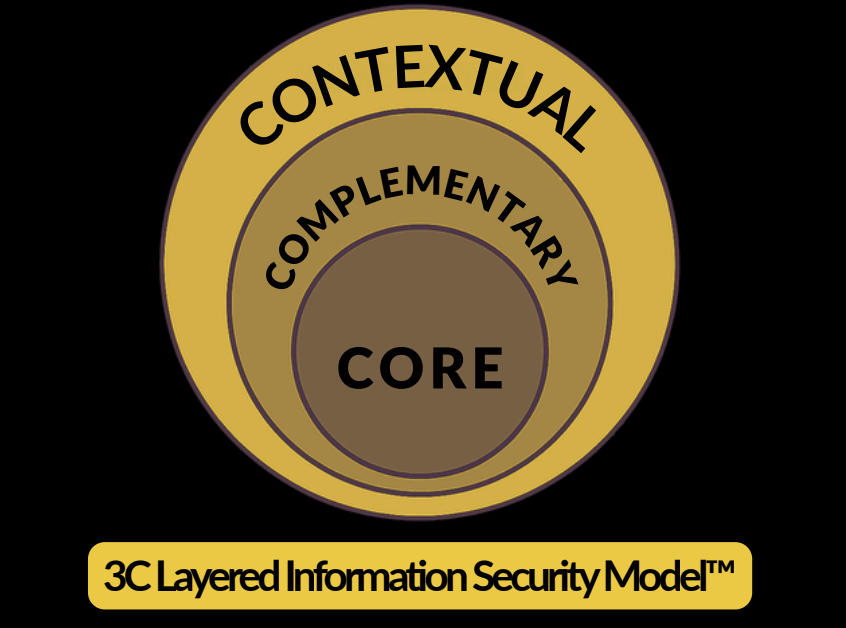
My mental model: 3 layers, not 3 letters
Think of security like a building:
-
Core — the load-bearing stuff. This is where CIA still lives, but I elevate three more: Authenticity (prove who/what something is), Accountability (irrefutable evidence of what happened), and Resilience (engineered recovery, not wishful uptime).
-
Complementary — the connective tissue that turns tech into duty: Privacy, Provenance/Traceability (what data and components went into this thing), Risk & Assurance (evidence, audits), and Transparency (can you explain the decision your AI just made).
-
Contextual — the “so what” to real humans and operations: Safety, Possession/Control, Utility/Fair Use, and Ethics/Human Impact. This is where “don’t blow up the factory floor” lives.
If the Core is weak, the rest is theater. You can’t regulate your way out of bad identity or mutable logs.
What this changes in the real world
-
Identity moves from best practice to non-negotiable. Phishing-resistant MFA for humans, strong identities for services and machines. If you can’t prove who touched what, nothing else matters.
-
Logs you can’t tamper with. If your crown-jewel systems don’t have immutable, chain-verified logging with sane retention, you’re arguing about shadows. Accountability is evidence, not vibes.
-
Backups that actually restore. Immutable copies, isolated recovery, and practiced drills. “We have backups” doesn’t count until you’ve rebuilt a production-scale app under stress and a stopwatch.
-
SBOMs like seatbelts. You ship software? Generate a Software Bill of Materials in the build. Consume software? Demand one. It’s not about buzzwords; it’s about knowing what you just let into your blast radius.
-
Governance that’s real, not paperwork. Privacy by design, data lineage, third-party risk—all mapped to your Core capabilities. If your privacy promises can’t be enforced by controls, it’s marketing.
But isn’t this just NIST/ISO/Zero Trust with a new hat?
Sort of—and that’s the point. We’re drowning in frameworks. What’s been missing is a clear dependency chain and a way to tell a coherent story:
-
Core: prove the system is truthful and survivable.
-
Complementary: prove you’re meeting your obligations.
-
Contextual: prove you won’t harm people or operations.
It’s not a new checklist. It’s a way to organize the ones you already have so priorities and funding align with reality, not with whoever shouted last.
The 90-day version (how I’d actually run this)
-
Days 0–15: Tag what you already do to the three layers. Don’t overthink it. You’ll instantly see gaps and duplications.
-
Days 16–45 (Core sprints):
-
Push phishing-resistant MFA to admins and high-risk users.
-
Turn on immutable logging for Tier-0/Tier-1 systems.
-
Make at least one Tier-1 app restorable from immutable backups in a clean room. Prove it with a timed drill.
-
-
Days 46–75 (Complementary sprints):
-
Start generating SBOMs in your CI/CD. Require them from your top 10 vendors.
-
Standardize DPIA intake and publish turnaround SLAs.
-
Pick five metrics with targets (not just metrics: owner + threshold).
-
-
Days 76–90 (Contextual reality check):
-
Pick one actual business outcome—e.g., “no safety incidents on Line 3 if the MES goes down.” Map it to the dependencies below, and fund the deltas.
-
If you can’t fit it on a single page for the exec team—three boxes, a few targets—start over. The point is clarity, not ceremony.
What I love about this approach
It lets me talk to everyone in their language without dumbing it down. Engineers get why identity, logs, and recovery come first. Legal and GRC get their proof and processes. Executives get a simple view of “will we survive the week, will regulators be happy, will customers trust us.” Same story, three floors.
What still annoys me
-
The “meta-framework” magic only works if someone maintains the mappings. Put it in Git, give it versions, assign an owner, review quarterly. Otherwise it’s just pretty talk.
-
The Contextual layer can become a junk drawer. Assign clear owners
-
Metrics without targets are theater. Every metric needs an owner, source of truth, baseline, target, and a page-me threshold.
Final word
CIA isn’t wrong—it’s just incomplete. If you want a security program that survives contact with modern reality, build Core truth, bind it with Complementary duty, and measure what it means in Context. Three layers. Clear dependencies. No drama.